Cybersecurity refers to the defensive measures that can be employed in the effort to protect digital assets—including enterprise systems, networks, programs, and data—from a wide range of risks and cyber threats. These measures involve implementing a combination of technologies and procedures to thwart cyberattacks and minimize their impact.
The main goal of cybersecurity is to safeguard against unauthorized access, data breaches, and disruptions to your business operations. It acts as a strategic shield against malicious activities and the foundation of a solid digital infrastructure, making your organization more resilient against cyber threats.
Let’s delve deeper into what cybersecurity is, the different types and categories of threats, and how you can guard your organization against them.
Table of Contents
Featured Partners: Cybersecurity Software
3 Core Principles of Cybersecurity
The foundation of cybersecurity rests on three core principles: confidentiality, integrity, and availability. Together, these principles are known as “the CIA triad” and are regarded as the central components of cybersecurity. They ensure the protection of the entire IT infrastructure through robust security protocols, as follows:
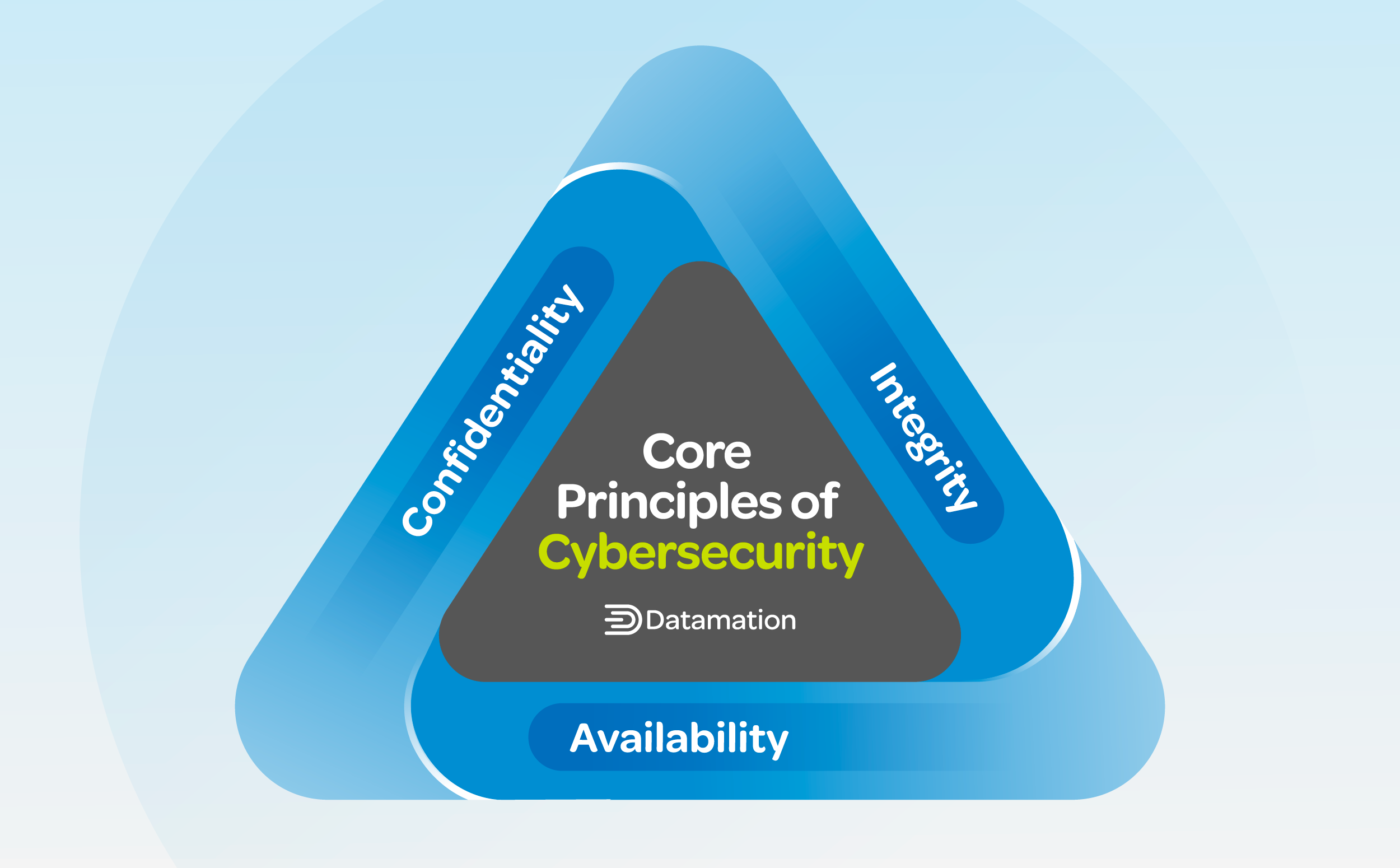
- Confidentiality: Confidentiality guarantees that sensitive information is accessed only by authorized individuals or systems, thus safeguarding against unauthorized disclosure.
- Integrity: This principle makes sure that data remains accurate and unaltered throughout its lifecycle, preventing unauthorized modifications and preserving trustworthiness.
- Availability: Availability ensures that information and resources are readily accessible to authorized users when needed, granting uninterrupted access to critical resources and services.
When combined, these principles lay the groundwork for effective cybersecurity management, emphasizing regulatory compliance, adoption of industry best practices, and risk mitigation. Keeping your organization safe from cyber threats can be arduous—prioritizing these core principles of cybersecurity enables your business to systematically identify and address risks, providing a structured methodology for managing security challenges.
9 Categories of Cybersecurity
Cybersecurity can be classified into nine categories to accurately address various aspects of digital security. Each category focuses on countering evolving threats. These categories cover different areas, using specific techniques and strategies to protect digital assets and infrastructure from malicious activities.
Network Security
Network security includes both software and hardware solutions to protect against unauthorized network access or service disruption. It requires implementing measures to detect, monitor, and defend against unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. It is a critical aspect of managing and maintaining infrastructure and usability of network systems.
Application Security
Application security safeguards applications and their data from unauthorized access and use. This category covers secure coding practices, encryption techniques, and thorough security testing. It’s not a one-off task, but a continuous process that’s integrated throughout the application’s lifecycle, from its initial design to its final deployment. Application security is an integral part of cybersecurity that protects your enterprise applications from threats.
Data Security
Data security protects digital information from unauthorized access, modification, or theft throughout its lifecycle—defending against malware and intrusions from third parties. It also involves the physical security of hardware and storage devices as well as the deployment of administrative and access controls. This category includes using cybersecurity techniques and data security tools to defend the privacy, wholeness, and readiness of digital assets, regardless of whether they are being stored or transferred.
Cloud Security
Cloud security is an aspect of cybersecurity that concentrates on safeguarding your organization’s cloud applications, data, and infrastructure. While cloud providers offer security solutions, they may not meet enterprise-grade standards, which often need additional third-party solutions. Management of cloud security is a shared responsibility between organizations and cloud service providers.
Endpoint Security
Endpoints—desktops, laptops, mobile devices, servers, and other connected gadgets, for example—serve as primary targets for cyberattacks. This type of cybersecurity covers cybersecurity measures like endpoint detection and response tools to prevent numerous threats and illegal access attempts. By securing endpoints, your organization can mitigate the risks of data breaches and maintain compliance with regulations.
Internet of Things (IoT) Security
IoT security is a comprehensive approach to safeguarding devices like smart thermostats and wearable fitness trackers. It entails identifying and categorizing these IoT devices, regulating their network activities through auto-segmentation, and applying Intrusion Prevention Systems (IPS) as a virtual safeguard against potential exploits. This strategy minimizes threats stemming from unpatched firmware and similar vulnerabilities.
Mobile Security
Mobile devices with access to enterprise information can make your company vulnerable to harmful software, unexpected security flaws, phishing, and attacks via instant messaging. Mobile security counters these threats, keeping the device and its operating system safe from danger. This ensures that only authorized devices that meet the company’s security criteria can access valuable resources.
Identity and Access Management (IAM) security
IAM security confirms and handles the identities of users, devices, and services to ensure only authorized entities have access to specific company resources to protect digital assets. digital identities, and their permissions within your organization. It employs a combination of strategies, technologies, and policies to minimize risks associated with identity access.
Zero Trust Security
Zero Trust Security is a modern security framework based on the principle of “never trust, always verify.” It operates on the assumption that all access requests, regardless of their origin, are potential threats. Zero Trust assumes potential threats may already exist within the network and requires continuous verification for every entity attempting to access resources. This approach differs from the traditional perimeter-focused model, which is inadequate in the era of cloud technologies and remote work.
Types of Cybersecurity Threats
Cybersecurity threats encompass a variety of malicious activities aimed at compromising enterprise systems and data. These threats target different types of infrastructure, including networks, endpoints, mobile or IoT devices, and even humans interacting with these technologies. The following table gives an overview of the varying types of cybersecurity threats and their usual targets.
| Type of Cyber Threat | Threat Category | Usual Targets |
|---|---|---|
| Malware (virus, worms, Trojans, ransomware) | Endpoint-based | Computers, laptops, smartphones |
| Denial-of-Service (DoS), Distributed Denial-of-Service (DDoS), Man-in-the-Middle (MitM) | Network-based | Routers, switches, servers |
| Zero-Day Threat | Software-based | Unpatched software, operating systems, applications |
| IoT Botnet | IoT-based | Smart home appliances or industrial sensors |
| SQL Injection, Brute Force Attack, Cross-Site Scripting (XSS) | Web application-based | Web applications, servers |
| Social Engineering, Phishing, Insider Threat | Human-based | Employees, users, stakeholders |
Endpoint-Based Threats
These threats directly target individual devices, posing risks to computers, laptops, smartphones, and other endpoint devices. Malware is an endpoint-based threat that aims to disrupt, damage, or gain unauthorized access to computer systems or data.
Viruses, worms, Trojans, and ransomware are the most common types of malware. Endpoints are vulnerable to malware attacks when they interact with infected files, software, or malicious websites.
Network-Based Threats
Network-based threats exploit vulnerabilities within a network infrastructure or devices like routers, switches, and servers. These threats negatively impact data integrity, communication channels, and the confidentiality of sensitive information. Network-based threats include the following:
- Denial-of-Service (DoS)/Distributed Denial-of-Service (DDoS) Attacks: These aim to impair a network or server’s functionality by saturating it with an overwhelming influx of traffic, leading to a denial of service.
- Man-in-the-Middle (MitM) Attacks: These threats eavesdrop on or manipulate the exchange of information by intercepting communication between two parties.
Zero-Day Threats
These target weaknesses in software or hardware that are not yet known to the vendor or have not been patched. Some people use zero-day vulnerability, zero-day exploit, and zero-day attack interchangeably, but it’s important to note their differences:
- Zero-Day Vulnerability: This refers to a previously undiscovered security weakness in software that a malicious actor can manipulate by injecting harmful code.
- Zero-Day Exploit: This is the technique that allows attackers to gain unauthorized access or cause harm to the system.
- Zero-Day Attack: This happens when a perpetrator releases malicious software to take advantage of a weakness in a software before the software vendor or developer gets the chance to patch the flaw.
IoT-Based Threats
IoT-based threats target Internet of Things (IoT) systems, which can include anything from devices to vehicles to smart buildings with software for data collection or exchange. The attacks aim to access sensitive data, typically by installing malware on the IoT device to cause damage. An IoT attack can infect your devices with malware.
IoT botnets are a major IoT-based threat. These are a collection of IoT devices that are under the control of cybercriminals. Attackers infect these devices with malware to launch DDoS attacks, steal data, and execute other cyberattacks.
Web Application-Based Threats
These take advantage of weaknesses in a web application’s coding. Also known as application-layer attacks, these threats can jeopardize the privacy and safety of sensitive personal information shared by users on your website. Web application based-threats include the following:
- SQL Injection: Malicious SQL code is injected into a web application’s input data. If the application fails to adequately cleanse this input, the malicious code could modify, remove, or disclose sensitive information from the database.
- Brute Force Attack: This is the systematic guessing and testing of different combinations of usernames, passwords, or encryption keys to gain unauthorized entry to a web application. Usually automated using software tools, this commonly attacks authentication protocols and uncovers hidden content within a digital platform to illegally access both individual accounts and larger network systems.
- Cross-Site Scripting (XSS): An attacker uploads a malicious script onto the website. This script, once embedded into web pages and viewed by other users, can steal data or perform other kinds of mischief.
Human-Based Threats
These threats arise from human actions, whether intentional or unintentional. Human-based threats occur due to negligence, lack of knowledge, or the weaponization of human psychological vulnerabilities. Examples of these threats include the following:
- Social Engineering: Uses psychological manipulation to trick people into revealing confidential data and capitalizes on human trust and error in digital interactions. A single deceived individual can give enough data for an attack impacting an entire organization.
- Phishing: Involves fraudsters tricking individuals into divulging passwords and personal details. Posing as a reliable source, they use emails, chats, texts, and calls to get you to reveal information they can misuse to access financial resources.
- Insider Threat: Arises from individuals with authorized access to an organization’s systems who can either intentionally or unintentionally cause harm through unauthorized data disclosure, sabotage, or espionage. Insider threats may not always be deliberate and may also originate from negligence or errors.
7 Common Risks of Poor Cybersecurity
Poor cybersecurity can lead to significant data breaches, financial loss, and legal repercussions for your company. Proactively address the risks of poor cybersecurity with effective security protocols to protect your digital assets and maintain the trust of stakeholders.
Data Loss
Lapses in end-user protection, employee vigilance, and password security can create opportunities for hackers to breach into your systems. Data breaches expose personal details, financial records, proprietary data, and other confidential material, which cybercriminals can either steal or compromise. Losing essential data related to customers, applications, or network operations can disrupt business continuity.
Operational Disruption
Cyberattacks can trigger system breakdowns and downtime and block access to vital data and applications. In extreme cases, a company might even need to isolate its entire IT infrastructure to limit the damage, conduct an investigation, and restore normal operations. These disruptions can lead to customer loss.
Productivity Decrease
Downtime from cyberattacks decreases productivity as employees are unable to complete their regular tasks until the problem is resolved and the systems are restored. In turn, this unplanned downtime adversely affects the entire operations, delaying production and transactions.
Regulatory Noncompliance
Inadequate cybersecurity measures can lead to breaches of data protection standards like those set by the GDPR and HIPAA. Such breaches can result in non-compliance penalties, such as fines and legal repercussions, depending on the severity of the violation.
Financial Loss
Poor cybersecurity can lead to financial losses in several ways. Cyberattacks can result in theft of sensitive data, including financial information and customer details, which can be sold or misused. Businesses may also face regulatory fines for failing to protect confidential data.
Additionally, disruption in business operations causes loss of revenue and even loss of customers. The cost of responding to an attack, covering investigation, remediation, and strengthening security measures, can also be substantial.
Reputational Damage
If a cyberattack results in a data breach, the trust that customers, partners, and stakeholders have in your organization can be seriously undermined. This may prompt customers to take their business elsewhere due to concerns about the security of their data. News of a cyberattack can also attract negative media attention, further damaging your organization’s reputation. The process of rebuilding trust and restoring the organization’s reputation can be time-consuming and costly.
Lawsuits
In the event of data breaches, victims often initiate class-action lawsuits seeking compensation for damages. The costs of legal fees and settlements can add up over time and become a financial burden for the business. Lawsuits also tarnish the company’s reputation, causing adverse media coverage and a diminished appeal to top talent.
Cybersecurity Best Practices
The following cybersecurity best practices serve as guidelines to fortify your defenses against different threats, ranging from data breaches to malicious attacks. By implementing these practices, you can boost your organization’s resilience against cyber attacks.
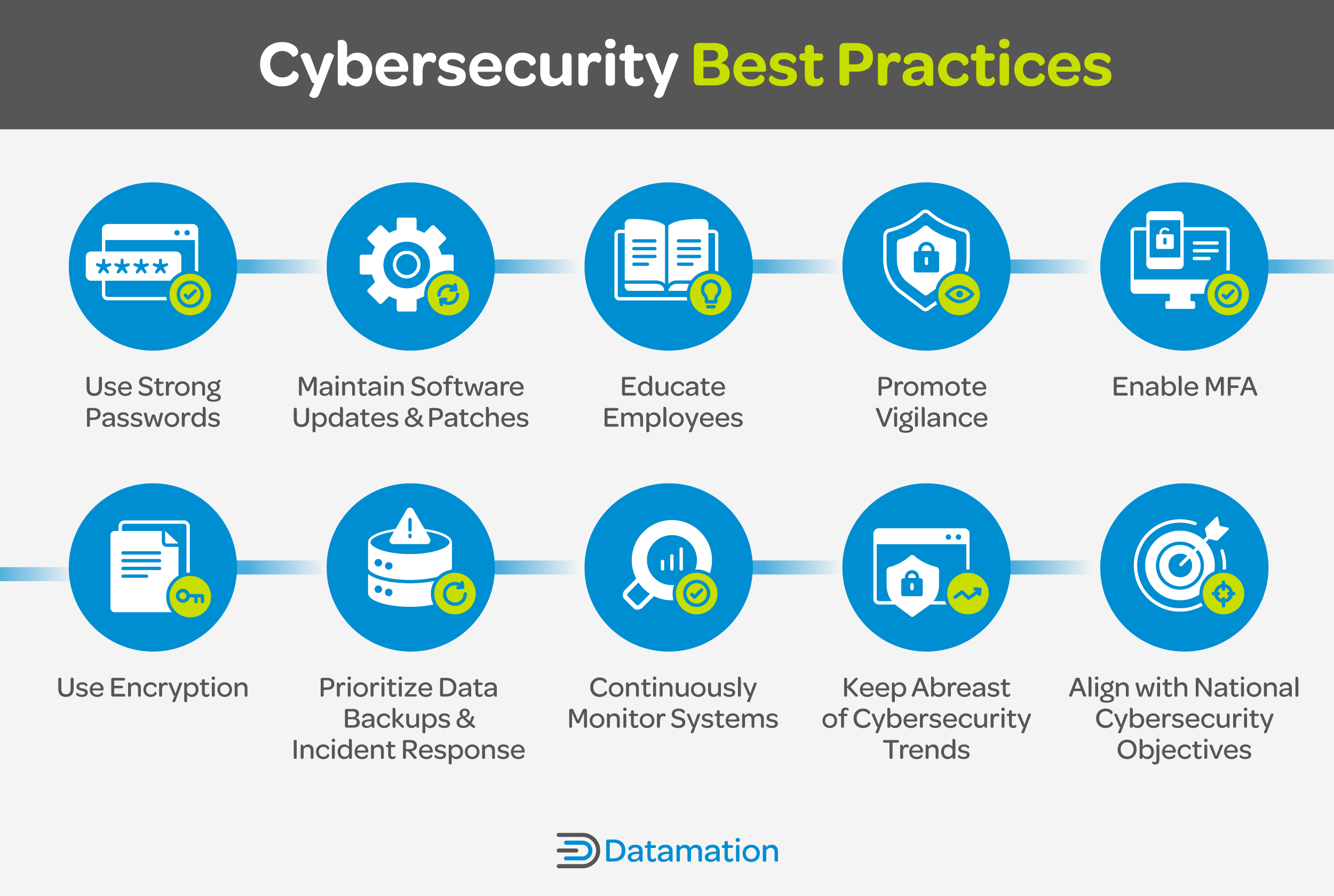
- Use Strong Passwords: Create complex passwords and use a combination of letters, numbers, and special characters, to heighten security and resist brute-force attacks.
- Maintain Software Updates and Patches: Ensure that all enterprise software and applications are regularly updated with the latest security patches to address known vulnerabilities and weaknesses, minimizing the risk of exploitation.
- Educate Employees: Invest in high-quality cybersecurity training and cybersecurity certifications to solidify knowledge and understanding among your employees. Keep an eye on the latest trends on cybersecurity training to find out the most critical topics to focus on.
- Promote Vigilance in the Workplace: Educate teams on exercising caution with suspicious links to prevent falling victim to phishing scams or malware infections.
- Enable Multi-Factor Authentication (MFA): Use MFA for an additional layer of security by requiring users to provide multiple forms of verification, like a password and a unique code sent to a mobile device, to reduce the risk of unauthorized access.
- Use Encryption: Encrypt sensitive data both in transit and at rest using robust encryption algorithms, and check proper management and protection of encryption keys to prevent unwanted access to your enterprise data.
- Prioritize Data Backups and Incident Response: Establish complete data backup procedures to create copies of critical information for restoration in case of data loss or ransomware attacks. Develop incident response plans to manage and mitigate cybersecurity incidents to secure business continuity and decrease the impact of breaches.
- Continuously Monitor Systems: Execute continuous monitoring practices to observe network traffic, system logs, and security events in real-time, enabling proactive detection and response to security threats.
- Keep Abreast of Cybersecurity Trends: Cyberattacks are getting more sophisticated each day—keep an eye on the latest trends and cybersecurity predictions to know what to expect in the future.
- Align with National Cybersecurity Objectives: Ensure that your cybersecurity efforts meet the goals outlined in the National Cybersecurity Strategy. By contributing to these objectives, you help improve the overall defense of your IT infrastructure.
Cybersecurity Measures: Tools for Enhancing Security
Using different cybersecurity tools as a measure to enhance your security will help keep your enterprise data, systems, networks, and customers safe. These tools each serve a specific purpose and work in harmony to create a strong defense against potential threats. The table below presents a summary of the most common cybersecurity tools used today, what they protect, and the usual threats they guard against.
| Cybersecurity Tool | Protected Entities | Threats Mitigated |
|---|---|---|
| Firewalls | Network | Unauthorized access, network attacks |
| Intrusion Detection Systems (IDS) | Network, Endpoints | Unauthorized access, intrusions |
| Encryption Software | Data | Unauthorized access, breaches |
| MFA Tool | User Accounts, Systems | Unauthorized access, credential theft |
| Patch Management Software | Software, Systems | Known vulnerabilities, exploits |
| Anti-Malware Software | Endpoints | Malware, viruses, Trojans, ransomware |
Firewalls
Firewalls are network security devices that monitor and filter incoming and outgoing network traffic. They come in various types, such as next-generation firewalls (NGFWs), stateful inspection firewalls, proxy firewalls, and unified threat management (UTM) firewalls. They act as a barrier between trusted and untrusted networks, protecting the network from unauthorized access and network-based attacks.
Intrusion Detection Systems
These monitor networks or systems for malicious activity or policy violations. They protect both network infrastructure and endpoint devices by detecting unwanted access and network intrusions, alerting the system or network administrators about potential threats. There are several types of IDS, namely network-based, host-based, protocol-based, application protocol-based and hybrid.
Encryption Tools
Encryption tools safeguard data by converting it into a coded format to deter illegal access, regardless of whether the information is stored on a device or transmitted over a network. Secure encryption techniques use data-scrambling methods to make decryption computationally infeasible without the appropriate cryptographic key. Common encryption algorithms are symmetric encryption—in which the same key is used for both encryption and decryption—and asymmetric encryption, which uses different keys for encryption and decryption.
Multi-Factor Authentication Software
These security systems demand multiple authentication methods from varied credential categories to confirm your identity. These could be email codes, one-time passwords (OTPs), biometric verification, or authenticator apps. By adding an extra layer of security, MFA software upholds protection against unauthorized access, credential theft, and other threats.
Patch Management Tools
These tools distribute and apply updates to software to improve functionality and correct security vulnerabilities. Patch management tools protect software and systems from known vulnerabilities and exploits, keeping them up-to-date.
Anti-Malware Software
These programs are designed to prevent, detect, neutralize, and remove malicious software on IT systems, networks, and individual computing devices. By constantly scanning for malicious activity and employing signature-based detection, heuristic analysis, and behavior-based algorithms, anti-malware solutions help defend against a range of cyber attacks.
Top 3 Cybersecurity Software Solutions
Dealing with cyber threats is not an easy task. A number of reliable cybersecurity solutions on the market can help you protect your IT infrastructure effectively. Here are some of the most widely used.
CrowdStrike
CrowdStrike’s AI-native cybersecurity platform includes real-time monitoring, threat intelligence integration, machine learning capabilities, and a single-agent solution. It also comes with firewall management, network detection services, vulnerability detection and management, and next-generation antivirus. CrowdStrike protects organizations with a singular lightweight agent that works in virtual machines, data centers, and even offline endpoints. Its cloud-native architecture simplifies deployment and cuts operational costs.
Cisco
Cisco is a renowned cybersecurity platform with a broad range of security solutions that include a firewall for advanced visibility and insights and a next-generation intrusion prevention system (IPS) for consistent protection against threats and malware. The vendor also offers products for email, cloud, endpoint, network, and workload security. Cisco Duo, its MFA offering, secures access to applications. Its Advanced Malware Protection performs real-time malware blocking and continuous analysis for quick detection and removal of threats.
Palo Alto Networks
Palo Alto Networks offers a platform with advanced firewalls and cloud-based security solutions. Its NGFWs classify network traffic by application identity for access control. Palo Alto security solutions integrate vulnerability protection, network anti-malware, and anti-spyware into one service, differing from traditional IPS. It also has built-in hardware crypto assist for encryption and an MFA feature. Palo Alto Networks’ PAN-OS software facilitates patch deployment for fixes without prolonged maintenance.
Bottom Line: What Is Cybersecurity?
Cybersecurity is not just a reactive approach—it’s a proactive strategy that protects digital assets by staying vigilant and following best practices as cyber threats continuously evolve. Implementing MFA, updating software regularly, and promoting security awareness bolsters defenses against potential breaches.
This guide is designed to help you gain a deeper understanding of cybersecurity and how you can protect your organization from the constant threat of cyberattacks with appropriate measures. Being proactive guarantees operational continuity, data confidentiality, and trust among your customers.
Read our article on companies hiring for cybersecurity jobs if you’re interested in starting a career in cybersecurity.





