Data security software solutions act as comprehensive shields against cyber threats, helping companies and organizations protect sensitive information including financial records and customer and other high-risk data. The best data security software takes a multi-layered approach to features that store and encrypt data, prevent malware infiltration, scan for vulnerabilities, and audit data security.
We evaluated the top software for data security on the market to see how it compares on key data and security management features to help you find the best option. Here are our picks for the best data security software for 2024:
The table below shows an overview of the essential features and pricing plans of the top data security tools. Note that only one provider made pricing info publicly available.
| Data Management Features | Security Management Features | Key Differentiator | Pricing | Free Trial | |
|---|---|---|---|---|---|
| FortiGate Next Generation Firewall |
|
|
Network-centric security | N/A | 30 Days |
| Acronis Cyber Protect |
|
|
Merges data backup and recovery capabilities | Starts at $85 per year | 30 Days |
| Bitdefender Gravityzone Business Security Enterprise |
|
|
Focuses on threat prevention | Contact sales to request a quote | 30 Days |
| Mimecast |
|
|
Specializes in email security | Contact sales to request a quote | 30 Days |
| Acunetix by Invicti |
|
|
Web application vulnerability scanning | Contact sales to request a quote | N/A |
| VMware Cloud Foundation |
|
|
Hybrid cloud infrastructure | Contact sales to request a quote | N/A |
| Sophos Intercept X |
|
|
Uses a mix of signature-based, behavioral, and AI-driven detection | Contact sales to request a quote | 30 Days |
![]()
Best Overall Data Security Software
FortiGate NGFW network security solution offers a unified platform for end-to-end security across complex hybrid environments. It’s designed to protect applications against a wide range of cyber threats by integrating advanced features such as intrusion prevention (IPS), web filtering, application control, and more. Fortigate NGFW operates on Fortinet’s FortiOS operating system, which provides users with deep visibility and security across multiple form factors.
Visit FortiGate NGFW
FortiGate NGFW runs on the FortiOS platform, which features dashboards with either a network operations center (NOC) or a responsive layout in which the dashboard fits all screen sizes, with columns determined by the size of the screen. On the NOC dashboard, columns are set but widgets can be resized both horizontally and vertically. The widgets in the dashboard are interactive. You can click and hover over most of them to see additional information or page links. You can also reorganize widgets by clicking and dragging them around the screen.
Fortinet recently launched its new FortiGate 3200F and 900G versions, enabling its data center to deliver high-performance capabilities and comprehensive threat protection across the entire infrastructure. This product upgrade combines FortiGuard AI-powered security services with data center protection against advanced threats. It also supports a unified management approach to protecting hybrid IT end-to-end solutions with hybrid mesh firewalls.
FortiGate NGFW enables businesses to create easy-to-use and customized protection across applications, devices, and individual employees, regardless of their location. It seamlessly integrates advanced networking and powerful security, providing industry-leading protection and custom application-specific integrated circuit (ASIC) technology that’s more advantageous than traditional network ASICs. This allows you to tailor your network security and performance against specific cyber threats that attack your business.
| Pros | Cons |
|---|---|
| Handles large traffic volumes | Learning curve for its centralized management interface |
| Available in various models for businesses and organizations | Some features are only available on the command-line interface |
| Intuitive graphical user interface (GUI) | Log services could be better |
Fortinet does not publish pricing but offers guidelines for what businesses can expect to pay for firewalls.
![]()
Best for Data Backup
Acronis Cyber Protect is a cybersecurity and data protection solution designed to safeguard businesses with a comprehensive backup and protection all-in-one management system. Acronis protects data, applications, and systems by integrating such features as data backup, disaster recovery, endpoint protection management solutions, and AI-based anti-malware.
Visit Acronis Cyber Protect
Acronis Cyber Protect has a clean interface with an easy-to-use dashboard and tools. On the left side of the dashboard, you can access different tabs and menus; clicking on them shows other options on the right side of the screen. If you have different services, you can easily switch between them by clicking on the tab on the upper part of the screen. You can also access more options through a drop-down menu in each row.
Acronis has recently upgraded its product to Acronis Cyber Protect 16, an AI-powered integration of data protection and cybersecurity. This latest product development combines backup, disaster recovery, AI-based malware, ransomware protection, remote desktop, and security tools in a unified platform. This upgrade lets the platform eliminate complexity, deliver new security capabilities, and keep costs down.
We picked Acronis Cyber Protect as ideal for data backup because of its standout features in data security and protection. You can rely on continuous data protection, which results in a shorter recovery time. Its security capabilities also prevent reinfection, giving you the ability to restore older files and technology with the latest updates, security patches, and anti-malware updates.
| Pros | Cons |
|---|---|
| Provides security to prevent reinfection | Separate cloud storage cost |
| Offers continuous protection for a shorter recovery time | Users report lackluster customer support |
| Tracks vital files and notifies for unbacked files | Web interface can sometimes be laggy |
Starts at $85 per year
30-day free trial available
Use Acronis Cyber Protect’s price calculator to estimate your cost.
![]()
Best for Endpoint Protection
Bitdefender GravityZone Business Security Enterprise is a multilayered security solution that provides businesses with endpoint protection. Multiple security layers include risk analytics and hardening; prevention; detection and response; reporting; and integration. This solution combines an endpoint protection platform with endpoint detection and response (EDR) capabilities to help users defend endpoint infrastructure such as workstations, servers, and containers throughout the threat lifecycle.
Visit Bitdefender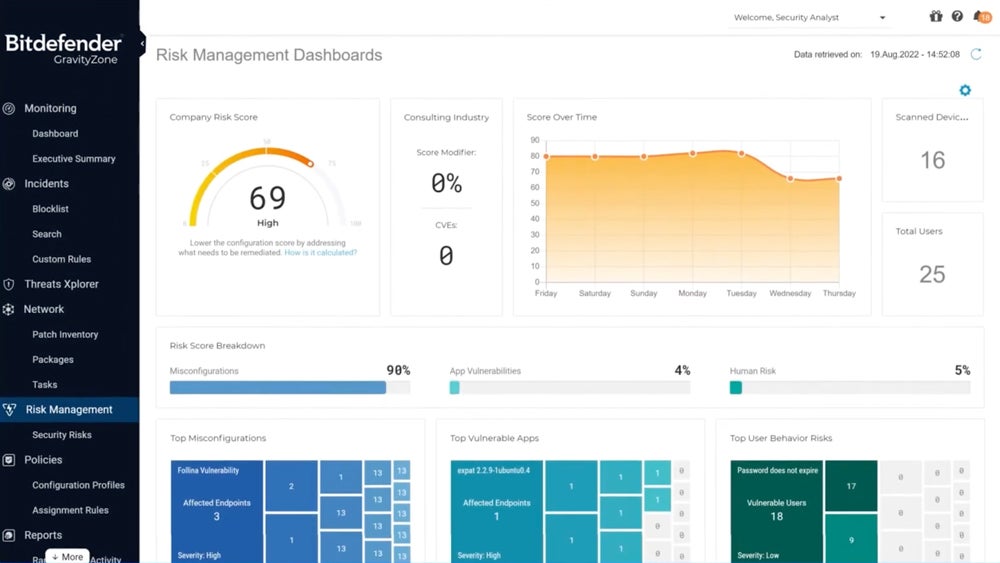
Bitdefender GravityZone has a clean interface displaying a list of tabs on the left side, which redirects you to different sections of the software. On each tab, you can access visual reports and actions that you can trigger.
Bitdefender GravityZone recently updated its power user module that’s available through the command line interface (CLI). This change reduces the disk size of the installed product, eliminating the Chromium dependency and supporting more GravityZone features. The company also rolled out new network protection features along with a live search feature that’s compatible with ARM64 architecture CPUs.
Bitdefender’s data security software, Bitdefender GravityZone Business Security Enterprise, is ranked as one of the best in the market. It stands out for effective endpoint protection using multiple layers of security techniques to stop cyberattacks throughout the entire system, from the first contact, exploit, persistence, or malicious activity that might occur. Its detection and response technology also provides threat visibility so your business can focus on investigating the vulnerabilities and determining how to respond.
| Pros | Cons |
|---|---|
| Robust encryption key management | Installation and deployment require a learning curve |
| Platform is constantly updated | Users report limited documentation |
| Blocks untrustworthy websites | Redesigned web console difficult to navigate |
Contact Bitdefender’s sales team to request a price quote.
![]()
Best for Email Security
Mimecast is a cloud-based application that offers advanced email and collaboration security, allowing organizations to avoid deploying dangerous tasks. This data security solution can combat common threats like viruses and malware and provides data security protection from advanced attacks like phishing and spear-phishing. It also protects against whale phishing, which uses dangerous links or attachments to trick users into sharing credentials, giving sensitive information, or transferring funds into cyberattacker accounts.
Visit Mimecast
Mimecast has a clean and simple user interface to provide a bird’s-eye view of the platform’s features and services. For instance, Mimecast’s administration console dashboard only displays information relevant to your account, hiding sections with functionalities you are not using. You can also filter the notifications you’d like to receive and access a color-coded title and icon to help identify the severity of alerts.
Users who’d like to see email queues can view a graphical display of the volume of incoming and outgoing messages for the last 48 hours. You can interact with these displays by hovering over a data point showing the number of emails per category or displaying a pop-up menu for printing the graph and downloading the graph to a file type.
Mimecast has recently improved its restore and export feature for its Email Security Cloud Integrated solution, enhancing the platform’s user experience and functionality. This upgrade lets you restore items to their original location or another nominated user, or export the items to a personal storage table (PST) file format. Additionally, its Email Security Cloud Gateway has also released QR code scanning capability, which helps upi identify QR codes in the body of an email and extract the URL for deep scanning. Its enhanced ‘quishing’ protection will also help keep inboxes clean and organized.
Emails are one of the top attack vectors and demand the strongest possible protection. Mimecast blocks a wide range of email-borne attacks, including phishing, ransomware, social engineering, payment fraud, and impersonation. It also helps prevent targeted attacks as it scans all emails in real time to check for links, dangerous attachments, and more. If the emails have potential threats, they will be rejected, or you will be sent a review via email.
| Pros | Cons |
|---|---|
| Able to maintain customer brand awareness | Platform can be complicated to use without experience |
| Robust management console | Pricing plans aren’t transparent |
Contact Mimecast’s sales team to request a quote.
![]()
Best for Automation
Acunetix by Invicti is a vulnerability scanner to help businesses keep their networks safe. Acunetix can automatically create a list of the company’s websites, applications, and APIs to ensure all covered items remain safe and updated. Acunetix can also detect more than 7,000 vulnerabilities with dynamic application security testing (DAST) and interactive application security testing (IAST) scanning, which makes it easier for developers to find, fix, and prevent vulnerabilities and lets businesses automate regular scans.
Visit Acunetix by Invicti
Acunetix by Invicti has a highly visual and colorful dashboard that makes it easy for users to view different charts and graphs. The panel at the top window shows you tabs for users, websites, completed scans, and active issues. It also features a website group drop-down feature that displays the security status of your websites or specific groups. You can also view various graphs, charts, and tables in the windows below the panel. The panels show severity trends, issues, average time to fix, and more.
Acunetix scans run very fast, but full scans of all targets may take some time. Acunetix recommends that you keep track of vulnerability checks that have been introduced or updated and store them in a scan type called new web vulnerabilities. Updates come out, on average, every month—you can view the Acunetix update changelog online.
Acunetix helps businesses avoid false positives that create unnecessary work for teams. This platform helps you automate web vulnerability assessment and management processes with precision, enabling teams to work more efficiently and reduce costs. Aside from its robust automation feature, Acunetix connects to continuous integration/continuous deployment (CI/CD), issue trackers, web application firewalls (WAFs), and other tools to improve the overall health of a network. Most scanners may not include this, but it is a proactive tool to support data security. Additionally, Acunetix has coverage using both DAST and IAST scanning to ensure full coverage for every web application, network, and data.
| Pros | Cons |
|---|---|
| Identifies a wide range of web vulnerabilities | Pricing structure isn’t transparent |
| Users can gain full visibility with comprehensive reports and dashboards | Users report slow customer support |
![]()
Best for Multi-Cloud Flexibility
VMWare, now part of Broadcom, is a leading data security software that protects against advanced and persistent threats across multi-cloud environments. The company retired its standalone VMWare NSX product and its data security software, which included a firewall, network switch, router, and load balancer to streamline security, and has made it available as part of the VMware Cloud Foundation.
VMWare Cloud Foundation lets you deploy a cloud operating model that integrates the scale of a public cloud with the security and performance of a private cloud. This new product features features such as cloud-scale networking, cloud management, infrastructure as a service (IaaS), and more.
Visit VMware Cloud Foundation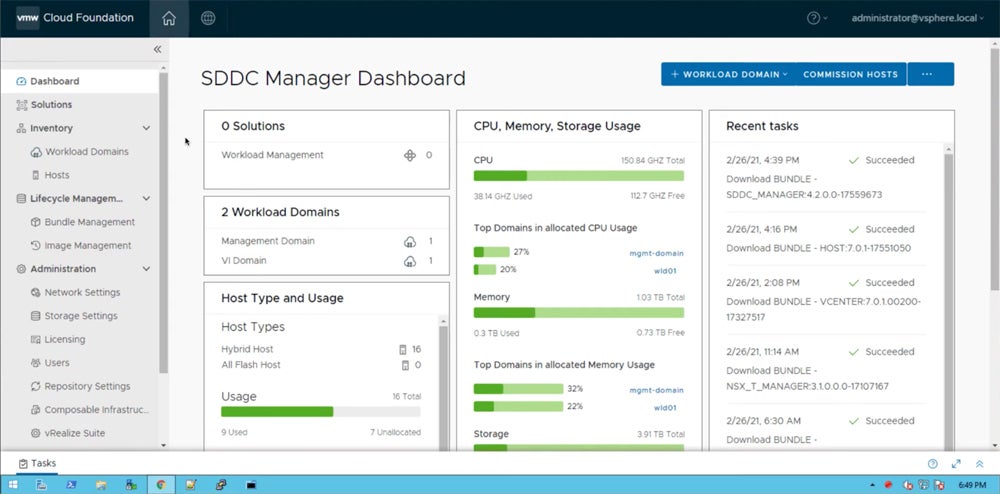
VMWare Cloud Foundation SDDC (software-defined data center) Manager provides a web-based interface where you can manage the platform. It offers unified access to the physical and virtual infrastructure of your system. Additionally, you can use this user interface (UI) to manage tasks associated with the VMWare software component.
VMWare Cloud Foundation recently released its intelligent network visibility, which provides information on the use of a network analysis tool enabling you to build an optimized and secure network infrastructure. It also adds features for identity and access management, health reporting and monitoring, intelligent logging, and more.
We chose the VMware Cloud Foundation because it helps users standardize management across multiple clouds through consistent infrastructure and operations. You can use familiar tools for different environments, from private cloud to public cloud, ensuring consistent operations across hybrid and multi-cloud environments.
| Pros | Cons |
|---|---|
| Versatile features for multi-cloud environments | Setting up can be challenging and complicated |
| Easy integration with VMWare’s ecosystem | Pricing plans aren’t transparent |
![]()
Best for Advanced Malware Blocking
Sophos Intercept X is an endpoint security solution that helps businesses respond to advanced cyberthreats, including known and unknown malware. It integrates signature-based detection, behavioral analysis, and AI-powered strategies to provide a multi-layered approach that lets you analyze files, web pages, and IP addresses to block access to phishing and malicious sites. This platform also uses threat intelligence from SophosLabs and real-time intelligence from Sophos MDR.
Visit Sophos Intercept X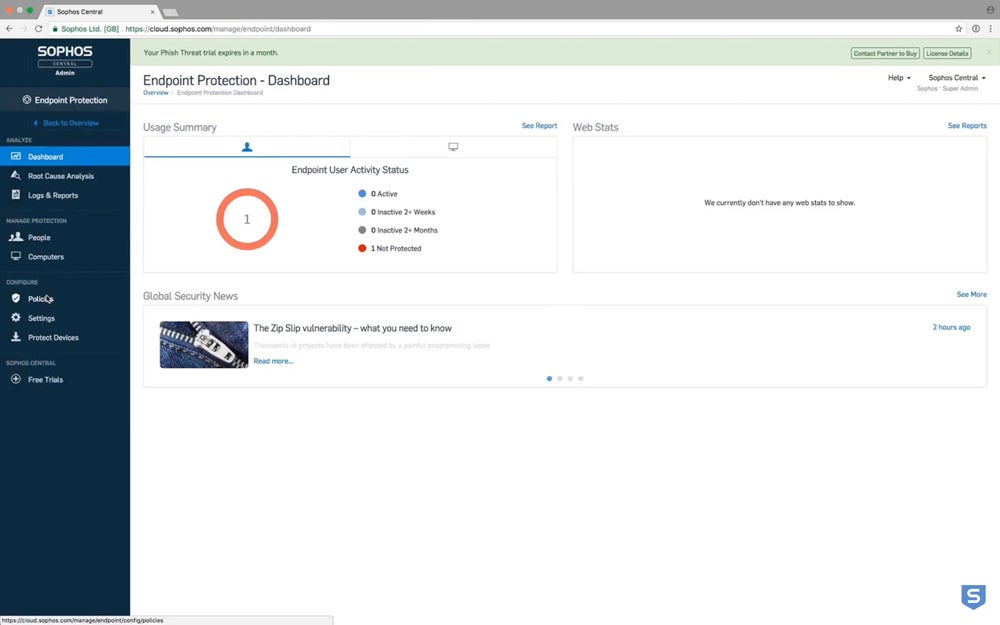
Sophos Intercept X has an easy-to-use interface that allows users to easily manage any device, application, and network security. You can use your mobile devices to perform security compliance checks with features like screen lock, encryption status, jailbreak, and more. For users navigating through a mobile app, Sophos Intercept X can block malware and ransomware, including potentially unwanted applications (PUA). Additionally, users accessing a network can rely on the platform to block malicious websites, unsafe download links, and more.
Sophos Intercept X has introduced several changes to the platform, including a ground-up rewrite of most functionalities to reduce footprint. The new architecture reduces the size of the Intercept X agent (memory footprint, services, and driver) without compromising quality and performance. The platform also has smaller updates to reduce bandwidth consumption and consume less disk space on update cache servers.
We picked Sophos Intercept X because it offers one of the most robust ransomware protections on the market. It uses behavioral analysis to block previously unseen ransomware and boot record attacks. It also offers layered defense with its multiple detection engines to catch a wide range of malware, which might not be identified if you only use signature-based tools. Moreover, its zero-day protection helps identify suspicious activities even without known malware signatures.
| Pros | Cons |
|---|---|
| User-friendly interface | Platform can be resource intensive |
| Zero-day malware protection | Core security products are sold separately |
Data security software has a number of important features, including data activity monitoring, automated reporting and risk analysis. Here’s a look at some of the most important to look out for when considering systems.
Sensitive information can reside in databases, data warehouses, big data platforms, and cloud environments. All need their data protected through automation by identifying sensitive information and assessing and minimizing the risk of data loss.
Monitoring tools can analyze users’ data usage patterns to let security teams see what users are accessing data and identify any possible risks. Data security software can block and alert customers in the case of abnormal activity.
Data security assessments used by data security tools make the process of detecting and solving risks such as misconfigurations, weak passwords, and the software identifies the most sensitive and at-risk data.
Data security software with automated capabilities can provide an extra level of safety. By automating risk protection, companies can save time and company resources.
Whether a company’s data is stored on-premises, in a data center, or in the public cloud, companies need to ensure that the data storage is secured against cybercriminals and has strong fire suppression measures. Cloud providers will likely supply extra security measures so the customers do not have to do it themselves.
Data and sensitive information require control over who has access and who does not. Some employees may need one part while others need information separate from that part. This means granting access to databases, networks, and administrative account access must be thought out and put into a policy based on need.
In evaluating the top data security tools, we first determined the six main criteria for businesses and organizations needing a solution that offers robust features for data management, security, and compliance. We then identified the weighted score for each category and assigned each option a total score out of five. Lastly, we summed up the scores to find out the category winners and identify their specific use cases.
The best data security software offers a powerful suite of data management and security features, so we put the most emphasis on these criteria. We also looked into their data security compliance and cost, followed by their ease of use and customer support.
We evaluated core security features for each solution, including malware protection, ransomware remediation, firewalls, and web protection. Criteria Winner: Fortigate NGFW
We looked into capabilities focused on data management such as data encryption, warehousing, data loss prevention, data automation, and more. Criteria Winner: Fortigate NGFW
Here, we considered how each solution complies with compliance standards. Criteria Winner: Multiple winners
This assesses the pricing plans of each tool, including the starting cost, free trial or free demo (if available), billing options, and pricing transparency. Criteria Winner: Acronis Cyber Protect
We browsed through real user reviews across certified sites to see how they perceived each platform’s usability. We also looked into their knowledge bases, documentation, and resources. Criteria Winner: Fortigate NGFW, Sophos Intercept X
We looked into each data security tool’s customer support via live chat, phone, and email. We also considered user reviews and ratings across reputable and popular sites. Criteria Winner: Bitdefender Gravityzone Business Security Enterprise
Your choice of data security solution can be based on the classification of data, industry, cost, or your company’s preference. Whether cloud, data center, or on-premise, your company needs tools to cover such infrastructure and data needsas access management, user dashboards, risk assessments, and data storage. Small, medium, and large companies will have different needs, and different industries will need other tool capabilities.
While system security and data security are closely related, they address different aspects of protection. System security focuses on safeguarding the health of your systems and networks, which includes features such as vulnerability scanning, malware protection, and access management. On the other hand, data security emphasizes protecting the integrity and accessibility of the data stored in your system with capabilities for data encryption, data loss prevention, local backup, and more.
The four pillars of data security include the following:
Data security software gives more insight to discover and solve any risk of a data breach. Features such as access management, a user dashboard, risk assessments, and where the data is stored should be part of the data security software and what the company needs. The best data security tools provide a balance of data management and network security, allowing users to protect their data and their overall system as a whole. Read our independent review of the best data security solutions, sign up for free trials or demos, or join an active user community to seek advice on finding the best tool for your business.
For a deep dive into how big data security works including its benefits, difficulties, and ways to implement it, read our comprehensive guide on the challenges and solutions in big data security.

Datamation is the leading industry resource for B2B data professionals and technology buyers. Datamation's focus is on providing insight into the latest trends and innovation in AI, data security, big data, and more, along with in-depth product recommendations and comparisons. More than 1.7M users gain insight and guidance from Datamation every year.
Advertise with TechnologyAdvice on Datamation and our other data and technology-focused platforms.
Advertise with Us
Property of TechnologyAdvice.
© 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this
site are from companies from which TechnologyAdvice receives
compensation. This compensation may impact how and where products
appear on this site including, for example, the order in which
they appear. TechnologyAdvice does not include all companies
or all types of products available in the marketplace.