Enterprises deploy a wide variety of cloud compliance tools to maintain the security and integrity of the cloud environment. These platforms follow industry-recognized standards and regulations for cloud compliance and help organizations adhere to the legal laws governing cloud computing services. We evaluated the most widely used of these tools to see how they compared on features—here are our picks for the best cloud compliance tools:
The chart below provides a high-level look at how our top picks compared against key features. Note that each of the tools we evaluated includes a wide range of compliance frameworks, and vendors add new ones regularly. Be sure to check their websites for the most current list. Also note that all per-user prices are with a one-year commitment, unless otherwise noted.
| Automated Remediation | Real-time Visibility | Compliance Specifications | Automation Capabilities | Pricing (Annual) |
|
|---|---|---|---|---|---|
| Sophos Cloud Optix | Yes | Yes | NIST, DISA, SOC, ISO, HIPAA, GDPR, PCI-DSS, CIS, CIPA, CCPA, ASD, POPI, NYDFS, Ohio Data Protection Act, HITRUST | Cloud-based |
Free trials and product demos Customized pricing options |
| Drata | Yes | Yes |
Cyber Essentials, SOC 2, ISO, HIPAA, GDPR, PCI-DSS, CCPA, CMMC, Microsoft SSPA, NIST, FFIEC, CCM |
Cloud-based | Quote-based |
| Vanta | Yes | Yes | HIPAA, SOC2, ISO, GDPR, USDP, NIST, FedRAMP, OFDSS, PCI-DSS, AWS FTR, MVSP, Microsoft SSPC, SOX, ITGC | Hardware, software, and hybrid | Customized plans |
| Sprinto | Yes | Yes | PCI-DSS, ISO, NIST, CSA, STAR, FCRA, OFDSS, CCPA, GDPR, HIPAA, AICPA, SOC2 | Cloud-based | Quote-based |
| Trend Micro Cloud One | Yes | Yes | ISO, CIS, LGPD, FISC, HITRUST, NIST, SOC2,APTRA,GDPR, HIPAA, PCIDSS, | Automated compliance and risk management processes | Contact sales for quote |
| PingSafe | Yes | Yes | PCI DSS, SOC 2, NIST, ISO 27001, HIPAA, GDPR | Automated compliance monitoring | Contact sales for quote |
| Wiz | Yes | Yes | NIST, HIPAA, CIS, HiTrust, SOC2, GDPR, FISMA, SOX, PCI DSS, FedRamp | Automated compliance | Quote-based |
| Cavirin | Yes | Yes | NIST, CIS 7, DISA, ISO, PCI-DSS, HIPAA, GDPR | Automated compliance and risk management processes |
Free plan Premium plan with a pay-as-you-go monthly pricing structure |
| Scrut Automation | Yes | Yes | GDPR, FERPA, SOC3, SOC2, ISO, NIST, PCI DSS, CSA STAR, HiTrust, CMMI SVC, CMMI DEV, HIPAA, FR | Automated risk assessment, automated remediation | Contact sales for quote |
| Secureframe | Yes | Yes | SOC2, ISO 27001, PCI DSS, Cyber Essentials, NYDFS NYCRR 500, FTC Safeguards Rule, Microsoft SSPA, NIST, CJIS, CMMS 2.0, HIPAA, GDPR, CCPA, CPRA | Automated compliance, automated evidence gathering, SOC2 automation | Quote-based |
![]()
Best for Public Cloud Environments
Sophos Cloud Optix is an artificial intelligence-powered security and compliance platform that enhances enterprise cloud protection and security management. It offers a single view of the entire compliance posture across all cloud environments and continuously assesses cloud configuration settings against complaints and security best practices standards. Sophos also has advanced reporting features with lists and graphs for visualizing compliance progress.
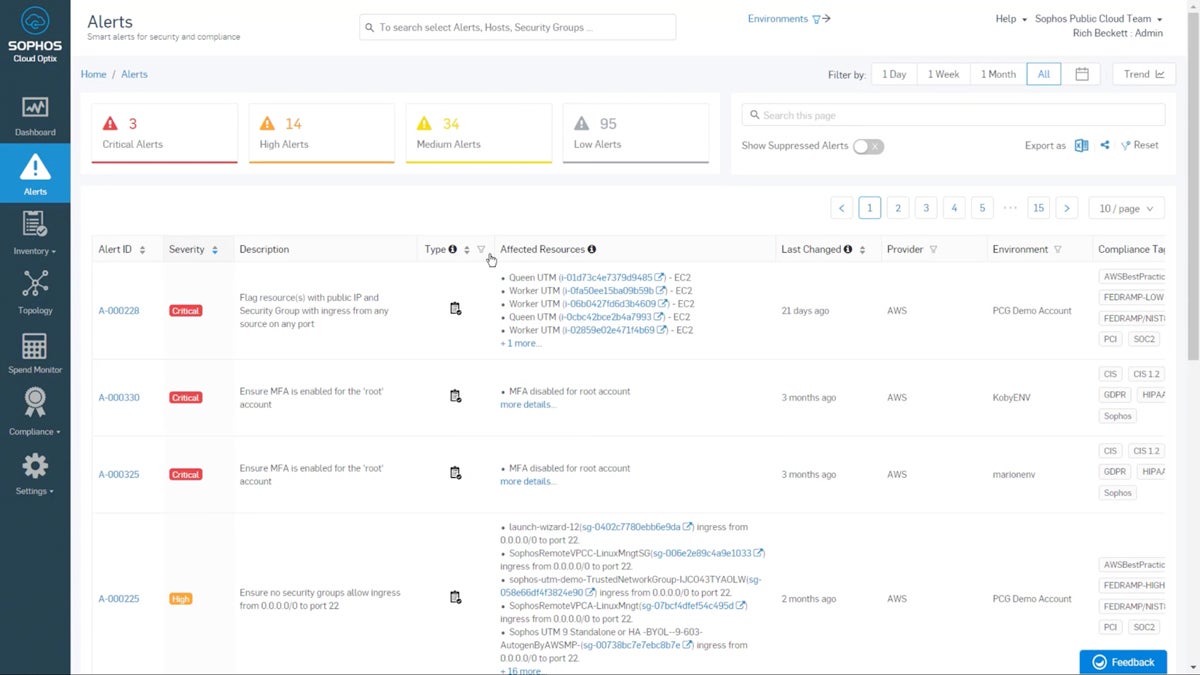
| Pros | Cons |
|---|---|
| Integrates with popular clouds like AWS, Azure, Google Cloud, and IaC | Cloud-only solution without provisions for on-premises deployments |
| Automatic remediation actions for detected threats | Demands hands-on-expertise and high-level technical knowledge |
![]()
Best for Compliance Automation
Drata is a leading solution for automated cloud compliance that uses a proprietary control library and supports a wide range of compliance frameworks. Businesses can use over 18 frameworks—including SOC 2, ISO 27001, and HIPAA—without sacrificing their need to tailor the platform according to their needs. Continuous automated monitoring provides a 360-degree view of compliance status and lets you address issues before they become a security crisis.
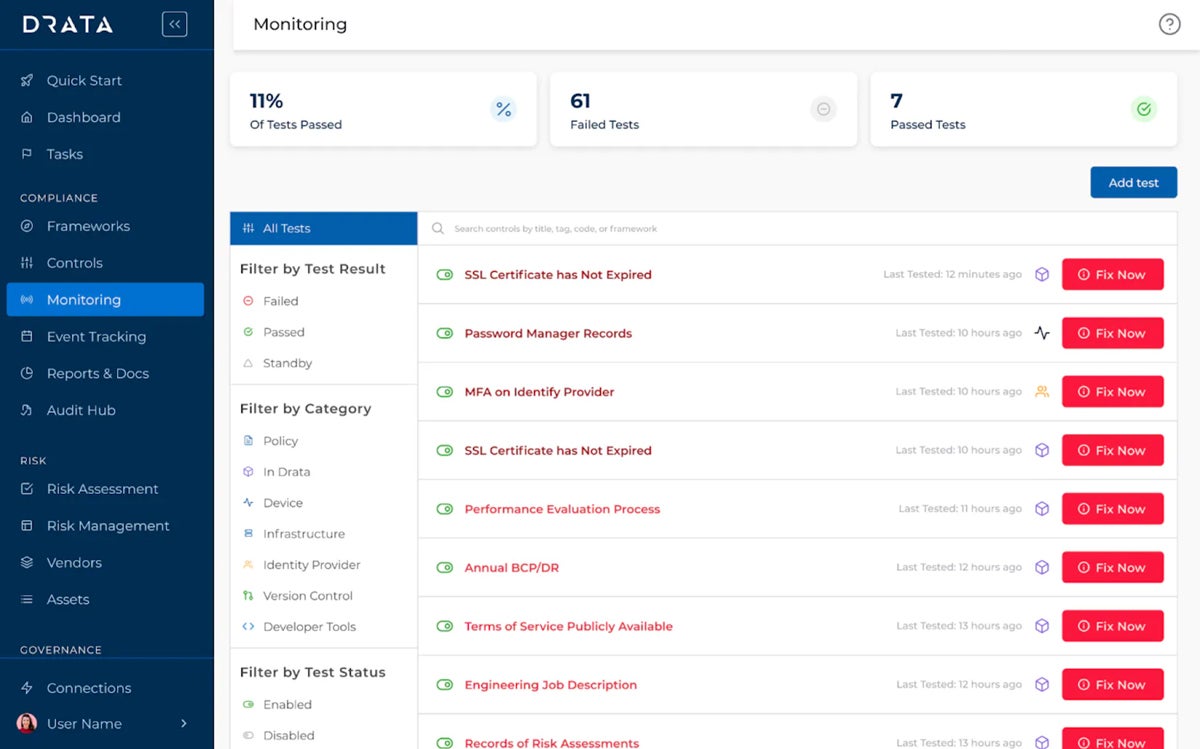
| Pros | Cons |
|---|---|
| Eliminates hundreds of hours of manual work | Setup can be confusing |
| Offers options for custom controls | Expensive pricing structure according to reviewers |
![]()
Best for SaaS Businesses
Vanta’s security and compliance platform offers a flexible and comprehensive compliance program with holistic risk visibility that helps SaaS businesses maintain a strong security posture and round-the-clock compliance. In addition to a wide range of compliance frameworks, it offers pre-built templates for creating custom policies—as a result, business practices can be translated into easy-to-track policies to check and monitor team compliance.
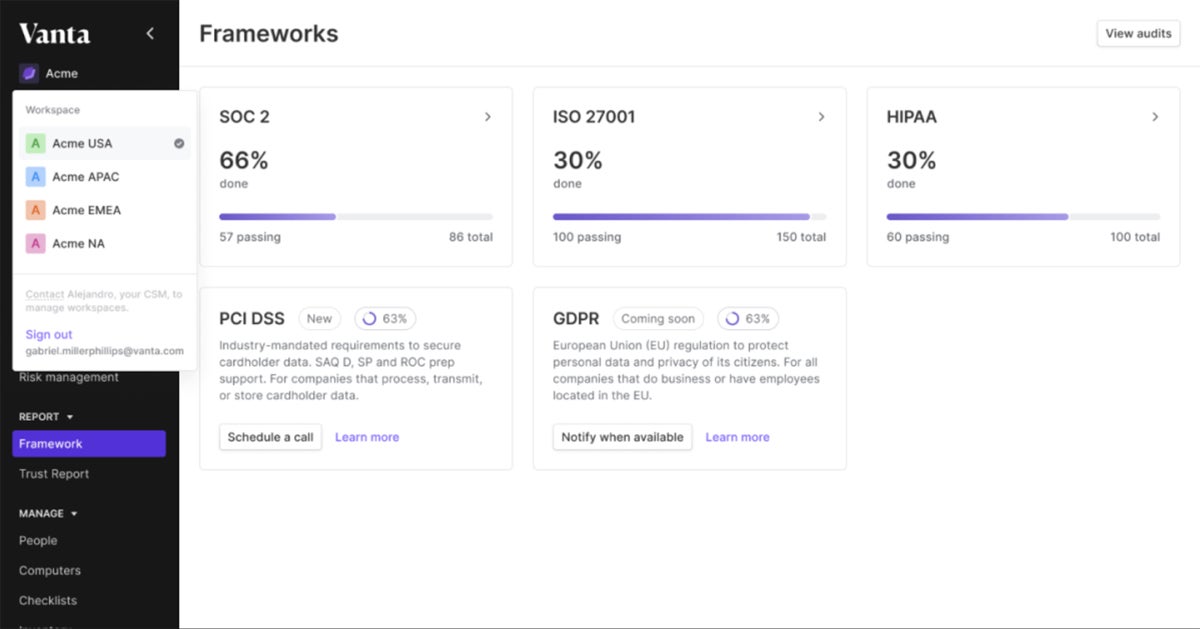
| Pros | Cons |
|---|---|
| Seamless audit process with a dashboard for tracking compliance progress | Some HD encryption settings get missed |
| Exclusive auditor portal for reviewing progress, checking evidence, and flagging issues | Requires more integration options for infrastructure monitoring |
| Streamlined third-party management for simplified vendor reviews | Documentation could be improved |
![]()
Best for Entity-Level Risks
Sprinto is a popular cloud compliance solution that controls and monitors entity-level risks. Its pre-approved, auditor-grade compliance programs can easily integrate across different cloud environments. Businesses can ensure that their data and systems are secured, and all cloud services work harmoniously with Sprinto’s entity-level mapping feature. Each employee also has unique credentials based on their roles, so they can only access specific data or areas.
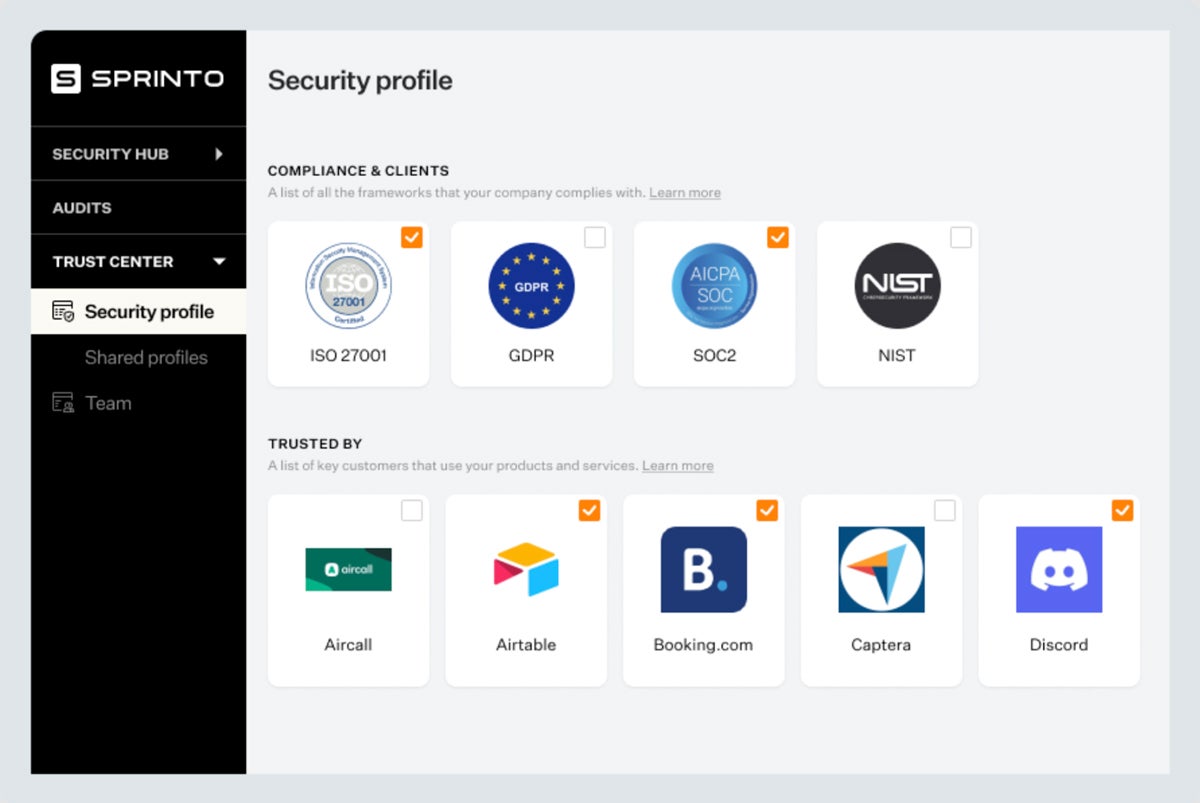
| Pros | Cons |
|---|---|
| Centralized security compliance management with an intuitive dashboard | Some users have experienced minor glitches in the UI |
| Expert-led implementation for stronger security and successful audits | Requires dedicated software for running in local systems |
| Widest compliance coverage with zero coordination chaos |
![]()
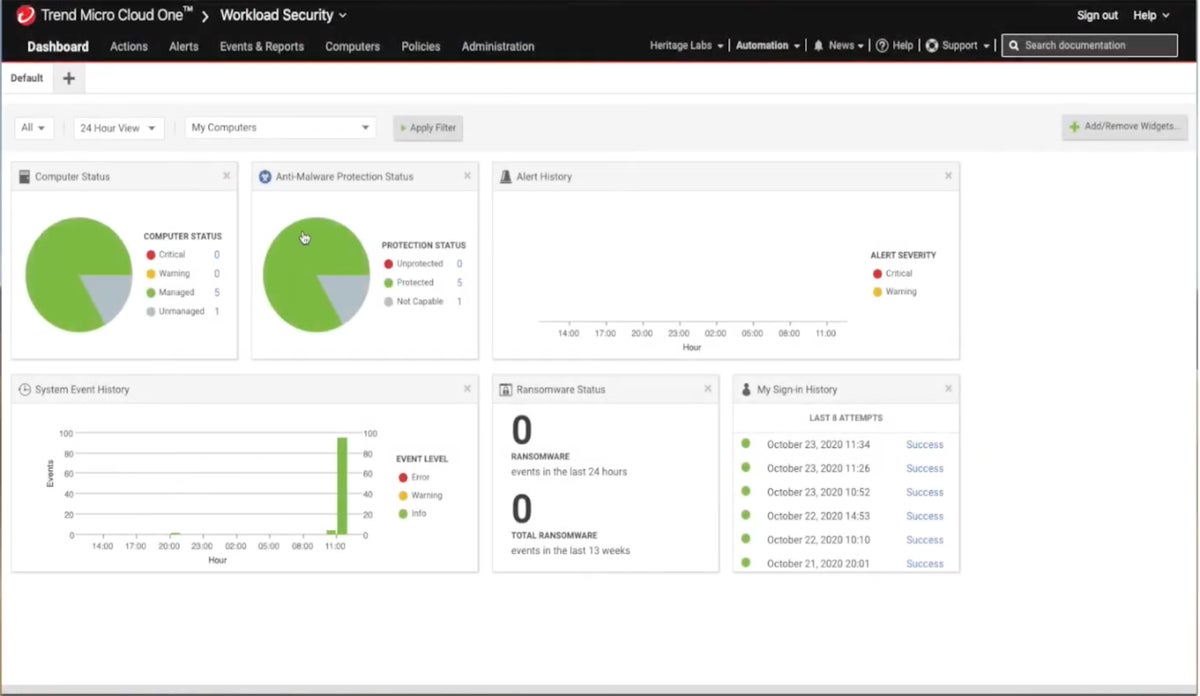
Best for Automated Security
Trend Micro Cloud One is a workload security solution that helps you optimize prevention, detection, and response for endpoints and workloads. Its strong API integration with Microsoft Azure, AWS, and Google Cloud and its workload security feature automatically protect existing and new workloads across different environments. Malware is also automatically scanned each time new files are uploaded without interrupting the development team’s workflows.
| Pros | Cons |
|---|---|
| Robust real-world malware protection | Technical support cloud be better |
| Automated compliance checks against a wide range of frameworks | Users report technical errors during upgrade |
![]()
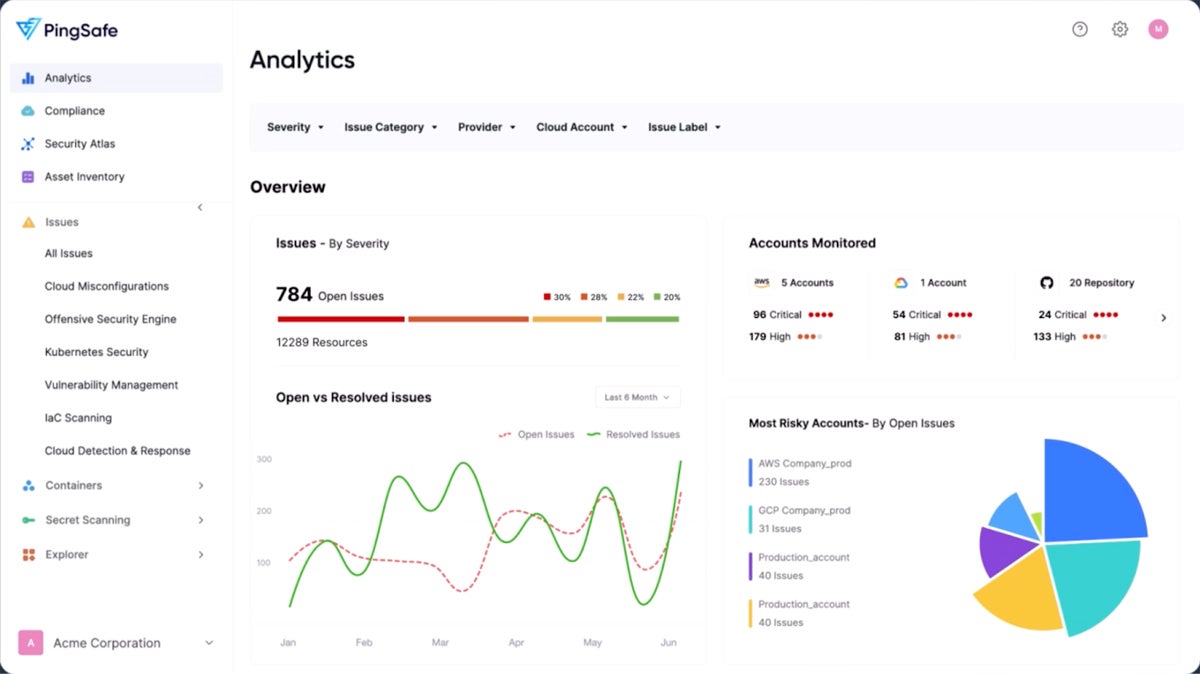
Best for Risk Alerts
PingSafe is a unified cloud security platform with real-time monitoring and risk-prioritizing alert tools. Leverage its monitoring capabilities to consistently scan the cloud and access complete attack surface visibility across multi-cloud infrastructures in one centralized location via its compliance dashboard. Access context-aware alerts, which are triggered by resource-specific contexts, so you can easily pull out actionable insights and address misconfigurations.
| Pros | Cons |
|---|---|
| Easy-to-use platform | Customer support could be better |
| Real-time monitoring features | Limited customization options |
![]()
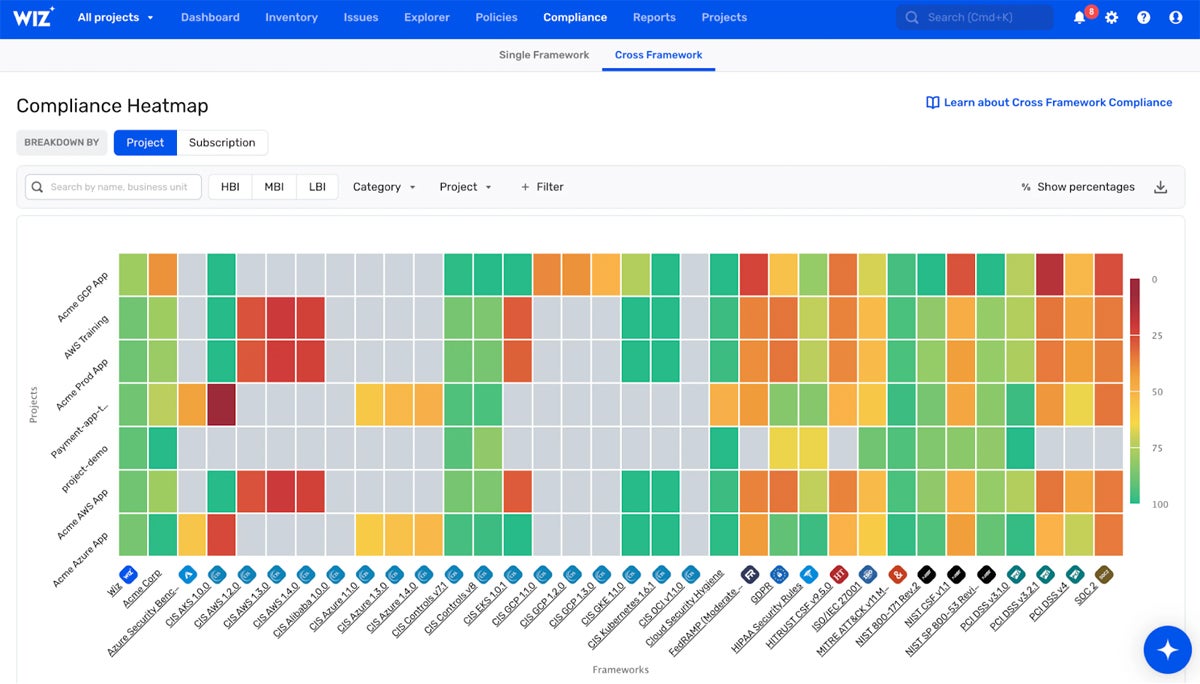
Best for Intuitive UX/UI
Wiz is a cloud visibility solution with a user-friendly platform that helps businesses connect to various cloud environments and cover cloud security issues. Its intuitive platform provides built-in cloud security solutions that normally require installing agents. Users can also take advantage of its security graph feature for straightforward and context-driven insights between the technologies running in their cloud environment with quick visualizations and analyses.
| Pros | Cons |
|---|---|
| Wealth of built-in cloud security tools | Limited pricing information |
| User-friendly dashboard | Remediation workflow could be better |
![]()
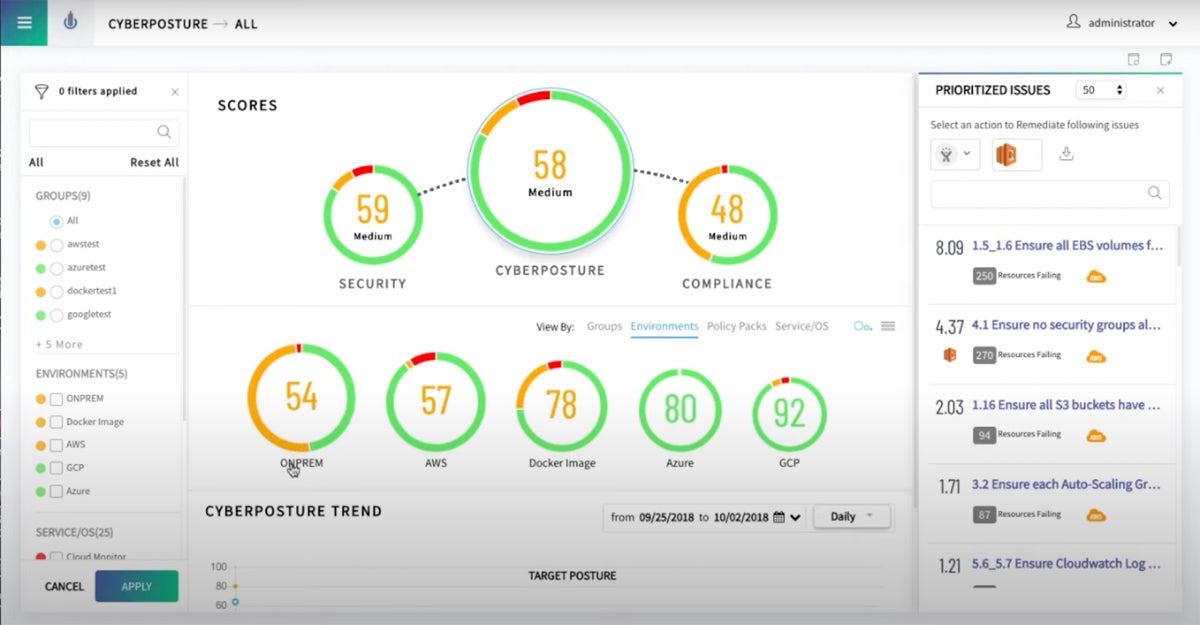
Best for Hybrid Cloud Platforms
Cavirin is a cloud compliance solution that provides cybersecurity risk posture and compliance for hybrid cloud platforms. Cavirin includes high-level features and benefits for hybrid cloud platforms, which can dynamically identify vulnerabilities and cybersecurity threats and fix cloud misconfigurations. Leverage its real-time monitoring, threat detection, and auto-remediation across platforms such as AWS, GCP, Azure, on-premises, Kubernetes, and more.
| Pros | Cons |
|---|---|
| Multiple regulatory compliance requirements for and centralized auditing information | Reporting features need improvement |
| Proactive security monitoring supported by recommendations and auto-remediation | On-premises CIS extension required |
![]()
Best for Cloud Native Companies
Scrut Automation is a risk-focused compliance automation platform that scans and monitors misconfiguration in cloud-native accounts such as AWS, Azure, Google Cloud Platform, and more. Users can test their cloud configurations automatically against more than 150 Center for Internet Security (CIS) benchmarks, build strong information security, and add customized controls to scan their platform instead of using CIS’s preconfigured standards.
An example of Scrut’s risk monitoring process. Source: https://www.scrut.io/
| Pros | Cons |
|---|---|
| Works with over 150 CIS benchmarks | Interface could be more intuitive |
| Responsive teams for support and onboarding | Users report occasional issues with cloud detection |
![]()
Best for Automated Evidence Collection
Secureframe is a security platform that allows businesses to automate evidence collection and end-to-end compliance tasks. Users can easily download all the evidence collected and generated through automated tests and operational tasks. Its data room feature enables you to run through collected evidence in bulk or individually at each framework and control. Securframe also highlights codes that should be prioritized for an easier remediation process.
| Pros | Cons |
|---|---|
| Wide range of prebuilt and customizable policies | Some workflows need automation |
| Robust and scalable platform | Users report minor bugs during integration |
The main objective of cloud compliance tools is straightforward: reduce cloud security risks without having to significantly alter existing business architecture. Here are the key considerations to consider when evaluating cloud compliance tools for your business.
The cloud environment demands continuous monitoring for security and compliance violations. Any breach, unauthorized access, or suspicious activity must be immediately reported to eliminate potential threats and attacks. Cloud computing tools must also offer unprecedented control and actively notify of any changes in the security and compliance protocols. Real-time visibility with centralized control and monitoring provisions can help improve the overall security level of the organization.
Detecting compliance violations can improve security, but remediation capabilities can boost its strength drastically. A good cloud compliance tool should help act to address security issues, eliminating manual intervention and proactively fixing misconfigurations.
There are many different compliance frameworks—including HIPAA, ISO 27001, NIST, GDPR, PCI, and DSS—that define specific cloud compliance requirements across industries and geographical locations. A cloud compliance tool must adhere to these standards and regulations without violations to avoid potential penalties. Some tools also enforce a wide range of compliance requirements or allow for customized frameworks.
Manual processes demand effort, time, and resources, and are prone to error—replacing them with automated workflows, scripts, or actions can enhance efficiency. Cloud compliance tools equipped with automation capabilities can trigger actions when non-compliance is detected.
Documenting compliance-related activities ensures transparency and accountability within the cloud environment and is essential for regulatory reporting and audits. A good tool offers a comprehensive view of the implemented compliance framework, security events, breaches, policy changes, fixes, and other associated events for future reference.
We assessed the top cloud compliance tools based on six major criteria and weighted subcriteria. We then included a five-point scale for each criteria and totaled the scores to determine the winner for each category and the best overall cloud compliance tool. Lastly, we assigned a primary use case to each cloud compliance tool included in our list.
We put the most weight on core features and compliance framework integration as cloud compliance tools deal with sensitive and confidential information. We then evaluated each option’s cost, customization, and ease of use. Finally, we looked into customer support solutions to wrap up our assessment of the best cloud compliance tools.
Here, we considered each tool’s key capabilities, including compliance management, data encryption, incident response, and monitoring. Criteria Winner: Sprinto
We looked into how each cloud compliance tool adheres to compliance frameworks such as GDPR, HIPAA, SOC 2, ISO 27001, and NIST. Criteria Winner: Multiple Winners
This considers the pricing plans offered by service providers including their starting license fee costs, free trial, billing options, and pricing transparency. Criteria Winner: Trend Micro Cloud One
We assessed the customizability of cloud compliance platforms for user roles, policies, and reporting tools. Criteria Winner: Vanta
We browsed through real user feedback and ratings across certified review sites to assess each tool’s usability and learning curve. We also looked into each option’s knowledge base. Criteria Winner: PingSafe
We considered user feedback from reputable sites to assess how each tool provides support via live chat, email, and phone. Criteria Winner: Sophos Cloud Optix
Cloud compliance tools can enhance the overall security posture of the business infrastructure, ensuring regulatory adherence. They also simplify compliance efforts for transparency. Non-compliance with government, regulatory agency, or other jurisdictional policy requirements can damage reputations, business, and bottom lines.
Service level agreements (SLAs) are legally binding contracts that define the terms and conditions associated with the delivered service between the client and the service provider. As businesses can also get compliance services from cloud service providers, it is important to use these legal agreements to avoid future conflicts.
There are a number of cloud compliance standards that vary based upon your business’s particular industry, but here are some of the most common:
Cloud compliance tools help companies adhere to compliance standards, automate monitoring processes, and facilitate the creation of custom internal policies and guidelines. While most cloud compliance solutions offer the standard features of compliance management, each platform differs in usability, customization, and framework integrations. Use our guide to narrow down your list of the best cloud compliance tools and find the best one for your business.
If you’d like to dive deeper into cloud compliance, including its considerations, services, and top service providers, read our comprehensive guide to cloud compliance.

Datamation is the leading industry resource for B2B data professionals and technology buyers. Datamation's focus is on providing insight into the latest trends and innovation in AI, data security, big data, and more, along with in-depth product recommendations and comparisons. More than 1.7M users gain insight and guidance from Datamation every year.
Advertise with TechnologyAdvice on Datamation and our other data and technology-focused platforms.
Advertise with Us
Property of TechnologyAdvice.
© 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this
site are from companies from which TechnologyAdvice receives
compensation. This compensation may impact how and where products
appear on this site including, for example, the order in which
they appear. TechnologyAdvice does not include all companies
or all types of products available in the marketplace.