Big data security is the process of monitoring and protecting a company’s important business data with the goal of ensuing safe and compliant ongoing operation.
Big data security is a constant concern because Big Data deployments are valuable targets to would-be intruders. A single ransomware attack might leave a company’s big data deployment subject to ransom demands. Even worse, an unauthorized user may gain access to a company’s big data to siphon off and sell valuable information. The losses can be severe. A company’s IP may be spread everywhere to unauthorized buyers, and it may suffer fines and judgments from regulators.
Securing big data platforms takes a mix of traditional security tools, newly developed toolsets, and intelligent processes for monitoring security throughout the life of the platform.
A Closer Look at Big Data Security
How Big Data Security Works
Big data security’s mission is clear enough: keep out on unauthorized users and intrusions with firewalls, strong user authentication, end-user training, and intrusion protection systems (IPS) and intrusion detection systems (IDS). In case someone does gain access, encrypt your data in transit and at rest.
This sounds like any network security strategy. However, big data environments add another level of security because security tools must operate during three data stages that are not all present in the network. These are: data ingress, which is what’s coming in; stored data; and data output going out to applications and reports.
Also read: Big Data Market Review 2021
Stage 1: Data Sources. Big data sources come from a variety of sources and data types. User-generated data alone can include CRM or ERM data, transactional and database data, and vast amounts of unstructured data such as email messages or social media posts. In addition to this, you have the whole world of machine-generated data including logs and sensors. You need to secure this data in transit, from sources to the platform.
Stage 2: Stored Data. Protecting stored data takes mature security toolsets including encryption at rest, strong user authentication, and intrusion protection and planning. A company needs to run its security toolsets across a distributed cluster platform with many servers and nodes. In addition, its security tools must protect log files and analytics tools as they operate inside the platform.
Stage 3: Output Data. The entire reason for the complexity and expense of the big data platform is so it can run meaningful analytics across massive data volumes and different types of data. These analytics output results to applications, reports, and dashboards. This extremely valuable intelligence makes for a rich target for intrusion, and it is critical to encrypt output as well as ingress. Also, secure compliance at this stage: make certain that results going out to end-users do not contain regulated data.
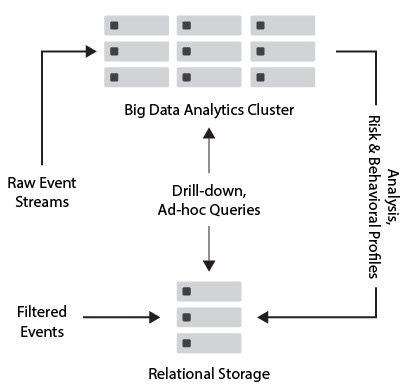
Big Data security is routed through a circuitous path, and in theory could be vulnerable at more than one point.
Navigating Big Data Security & Trends
Two of the biggest trends in the world of big data stand somewhat in opposition to each other: the proliferation of big data that informs smart technology, and also the growing movement for consumers to own and decide how their personal data is being used.
Technologies like IoT, artificial intelligence, machine learning, and even customer relationship management (CRM) databases collect terabytes of data that contain highly sensitive personal information. This personal form of big data is valuable for enterprises that want to better cater their products and services to their audience, but it also means that all companies and third-party vendors are held responsible for the ethical use and management of personal data.
As big data and its enterprise use cases continue to grow, most organizations work hard to comply with consumer data laws and regulations, but their security holes leave data vulnerable to breach. Take a look at some of the top trends happening in the big data world, the important security points that many companies are missing, and some tips for getting big data security right:
Update your cloud and distributed security infrastructure
Big data growth has caused many companies to move toward cloud and data fabric infrastructures that allow for more data storage scalability. The problem? Cloud security is often established based on legacy security principles, and as a result, cloud security features are misconfigured and open to attack.
For a company to navigate this requires speaking with cloud and storage vendors about their products, whether a security solution is embedded, and if they or a third-party partner recommend any additional security resources.
Set mobile device management policies and procedures
IoT and other mobile devices are some of the greatest sources and receivers of big data, but they also offer several security vulnerabilities since so many of these technologies are owned and used for personal life. Set strict policies for how employees can engage with corporate data on personal devices, and be sure to set additional layers of security in order to manage which devices can access sensitive data.
Provide data security training and best practices
Most often, big data is compromised as the result of a successful phishing attack or other personalized attack targeted at an unknowing employee. Train your employees on typical socially engineered attacks and what they look like, and again, set up several layers of authentication security to limit who can access sensitive data storage.
For more big data trends: Big Data Trends and The Future of Big Data
Benefits Of Big Data Security
With the benefits of customer retention, risk identification, business innovation, cost, and efficiency, a big data security system can be of value to companies everywhere.
Here are key benefits of big data security:
- Customer Retention: With big data security, a company can observe many data patterns, which allows them to better fit their products and services with their clients needs.
- Risk Identification: Because of big data security, a company can use big data tools to identify risks in their infrastructure, helping companies create a risk management solution.
- Business Innovation: Big data security can help companies update their tools and help transfer products into new secure systems. This innovation can improve business processes, marketing techniques, customer service, and company productivity.
- Cost Optimization: Big data security technologies can reduce customer costs by efficiently storing, processing, and analyzing large volumes of data. Big data security tools also will calculate how the product will benefit the company, so companies can pick a company that is better for their infrastructure.
For more information on data management: 5 Top Data Management Predictions
Challenges of Big Data Security
There are several challenges to securing big data that can compromise its security. Keep in mind that these challenges are by no means limited to on-premise big data platforms. They also pertain to the cloud. When you host your big data platform in the cloud, take nothing for granted. Work closely with your provider to overcome these same challenges with strong security service level agreements.
Here are the key challenges to big data security:
- Newer technologies can be vulnerable: Advanced analytic tools for unstructured big data and nonrelational databases (NoSQL) are examples of newer big data technologies in active development. It can be difficult for security software and processes to protect these new toolsets.
- Variable impact: Mature security tools effectively protect data ingress and storage. However, they may not have the same impact on data output from multiple analytics tools to multiple locations.
- Access without permission: Big data administrators may decide to mine data without permission or notification. Whether the motivation is curiosity or criminal profit, your security tools need to monitor and alert on suspicious access no matter where it comes from.
- Beyond routine audits: The sheer size of a big data installation, terabytes to petabytes large, is too big for routine security audits. And because most big data platforms are cluster-based, this introduces multiple vulnerabilities across multiple nodes and servers.
- Requires constant updates: If the big data owner does not regularly update security for the environment, they are at risk of data loss and exposure.
Big Data Security Technologies
None of these big data security tools are new, from encryption to user access control. What is new is their scalability and the ability to secure multiple types of data in different stages.
- Encryption: Your encryption tools need to secure data in transit and at rest, and they need to do it across massive data volumes. Encryption also needs to operate on many different types of data, both user- and machine-generated. Encryption tools also need to work with different analytics toolsets and their output data, and on common big data storage formats including relational database management systems (RDBMS), non-relational databases like NoSQL, and specialized filesystems such as Hadoop Distributed File System (HDFS).
- Centralized Key Management: Centralized key management has been a security best practice for many years. It applies just as strongly in big data environments, especially those with wide geographical distribution. Best practices include policy-driven automation, logging, on-demand key delivery, and abstracting key management from key usage.
- User Access Control: User access control may be the most basic network security tool, but many companies practice minimal control because the management overhead can be so high. This is dangerous enough at the network level and can be disastrous for the big data platform. Strong user access control requires a policy-based approach that automates access based on user and role-based settings. Policy-driven automation manages complex user control levels, such as multiple administrator settings that protect the big data platform against inside attacks.
- Intrusion Detection and Prevention: Intrusion detection and prevention systems are security workhorses. This does not make them any less valuable to the big data platform. Big data’s value and distributed architecture lend themselves to intrusion attempts. IPS enables security admins to protect the big data platform from intrusion, and should an intrusion succeed, IDS quarantines the intrusion before it does significant damage.
- Physical Security: Don’t ignore physical security. Build it in when you deploy your big data platform in your own data center or carefully do due diligence around your cloud provider’s data center security. Physical security systems can deny data center access to strangers or to staff members who have no business being in sensitive areas. Video surveillance and security logs will do the same.
Also read: How Big Data is Used: Business Case Studies
Implementing Big Data Security
Whether you’re just getting started with big data management and are looking for initial big data security solutions, or you are a longtime big data user and need updated security, here are a few tips for big data security implementation:
- Manage and train internal users well: As alluded to before, accidental security mistakes by employees offer one of the most frequently used security vulnerabilities to malicious actors. Train your employees on security and credential management best practices, establish and have all users sign mobile and company device policies, and offer only minimum-necessary data source access to each user based on their role.
- Plan regular security monitoring and audits: Especially in larger companies where big data and software grows on a near-daily basis, it’s important to regularly assess how the network and data landscape changes over time. Several network monitoring tools and third-party services are offered on the market, giving your security staff real-time visibility into unusual activity and users. Regular security audits also give your team the opportunity to assess bigger-picture issues before they become true security problems.
- Talk to a trusted big data company: Big data storage, analytics, and managed services providers usually offer some form of security or partner with a third-party organization that does. The platform that you use might not have all of the specific features that your industry or particular use cases require, so talk to your providers about your security concerns, regulatory requirements, and big data use cases so they can customize their services to what you need.
More on security implementation: Top 10 Ways to Prevent Cyber Attacks
Who Is Responsible For Big Data Security?
A big data deployment crosses multiple business units. IT, database administrators, programmers, quality testers, InfoSec, compliance officers, and business units are all responsible in some way for the big data deployment. Who is responsible for securing big data?
The answer is everyone. IT and InfoSec are responsible for policies, procedures, and security software that effectively protect the big data deployment against malware and unauthorized user access. Compliance officers must work closely with this team to protect compliance, such as automatically stripping credit card numbers from results sent to a quality control team. DBAs should work closely with IT and InfoSec to safeguard their databases.
Finally, end-users are just as responsible for protecting company data. Ironically, even though many companies use their big data platform to detect intrusion anomalies, that big data platform is just as vulnerable to malware and intrusion as any stored data. One of the simplest ways for attackers to infiltrate networks, including big data platforms, is a simple email. Although most users will know to delete the usual awkward attempts from Nigerian princes and fake FedEx shipments, some phishing attacks are extremely sophisticated. When an admin is administering security for the company big data platform, never ignore the power of a lowly email.
Secure your big data platform from high threats and low, and it will serve your business well for many years.
Read next: Top 10 Cybersecurity Threats
Big Data Security Companies
Digital security is a huge field with thousands of vendors. Big data security is a considerably smaller sector given its high technical challenges and scalability requirements. However, big data owners are willing and able to spend money to secure valuable employments, and vendors are responding. Below are a few representative big data security companies.
Snowflake
Snowflake’s team of data experts believe that data security should be natively built into all data management systems, rather than added on as an afterthought. Snowflake’s Data Cloud includes comprehensive data security features like data masking and end-to-end encryption for data in transit and at rest. They also offer accessible support to their users, allowing them to submit reports that Snowflake and their partner, HackerOne, can analyze while running their private bug program.
Teradata
Teradata is a top provider of database and analytics software, but they’re also a major proponent and provider of cloud data security solutions. Their managed service, called Cloud Data Security As-a-Service, offers regular third-party audits to prepare for data regulatory committee audits. They also offer features such as data encryption in transit and at rest, database user role management, storage device decommissioning, cloud security monitoring, and a two-tiered cloud security defense plan.
Cloudera
Cloudera’s primary strategy for big data security is to consolidate security management through their shared data experience (SDX), or to manage security and policies from a unified standpoint across all workloads. This means that even as tools and most frequently used workloads change over time, policy and security updates can still be managed centrally without siloes. Among their security solutions, Cloudera provides unified authentication and authorization, end-to-end visibility for audits, security solutions, data policy-specific solutions, and several forms of encryption.
IBM
IBM’s data security portfolio focuses on multiple environments, global data regulations, and simple solutions so that users can easily manage their data sources and security updates after deployment. Some of the main areas that IBM pays attention to for data security include hybrid cloud security management, embedded policy and regulation management, and secure open source analytics management.
Oracle
Oracle is one of the largest database hosts and providers in the big data market, but they also offer several top-tier security tools to their customers. Their security solutions focus on the following categories: security assessment, data protection and access control, and auditing and monitoring They also extend platform-specific security support for two of their most popular solutions, Autonomous Database and Exadata.
Hear from a Big Data Exec at Teradata: Ask an Executive: Data Analytics in Business
Bottom Line: Big Data Security
If a company uses well chosen big data security tools, these tools will serve the business well for many years, enabling it to secure its big data platform from threats of all kinds.
Big data security is changing continuously to help companies across all industries. Even with the many challenges, big data security benefits, easy implementation, and today’s advance big data security tools will help companies as they grow.
For more on data security: Top Data Center Security Software